Dating in Web3
by David An and Anies Khan, February 24, 2023
Does anyone remember the rating site HotorNot? Launched in October 2000 at the height of the Dotcom wave, it reached 2 million page views per day within weeks and became a Top 25 advertising domain within months. 23 years later, the site is dead but the popularity of online dating is still on the rise. Over the past 30 years, it has surpassed all other ways how heterosexual couples meet by leading with 40%. 30% of couples have met in a bar or restaurant. Only 20% have been introduced through friends today which declined from 35% in the eighties. Two-thirds of LGBTQ couples report having met online. But where is the industry heading? What are its next milestones? This article discusses whether Web2 Online Dating will be the next industry that will be disrupted by Web3 technologies. We believe this will happen, and show what potential key features a Web3 dating service, protocol or offering could or should include.
Source: Wayback Machine
Why is the Web2 Online Dating market relevant at all?
Globally, the industry has grown significantly. The market is expected to reach $10B in 2023 and expand at a CAGR of 6.9% from 2021 to 2030. There are 384M global users of which 311M are paying. Forecasts predict 440M users by 2027 with the USA being the largest market in terms of users (36%) and Asia having the highest growth rates at a CAGR 2022-2030. (additional source: here)
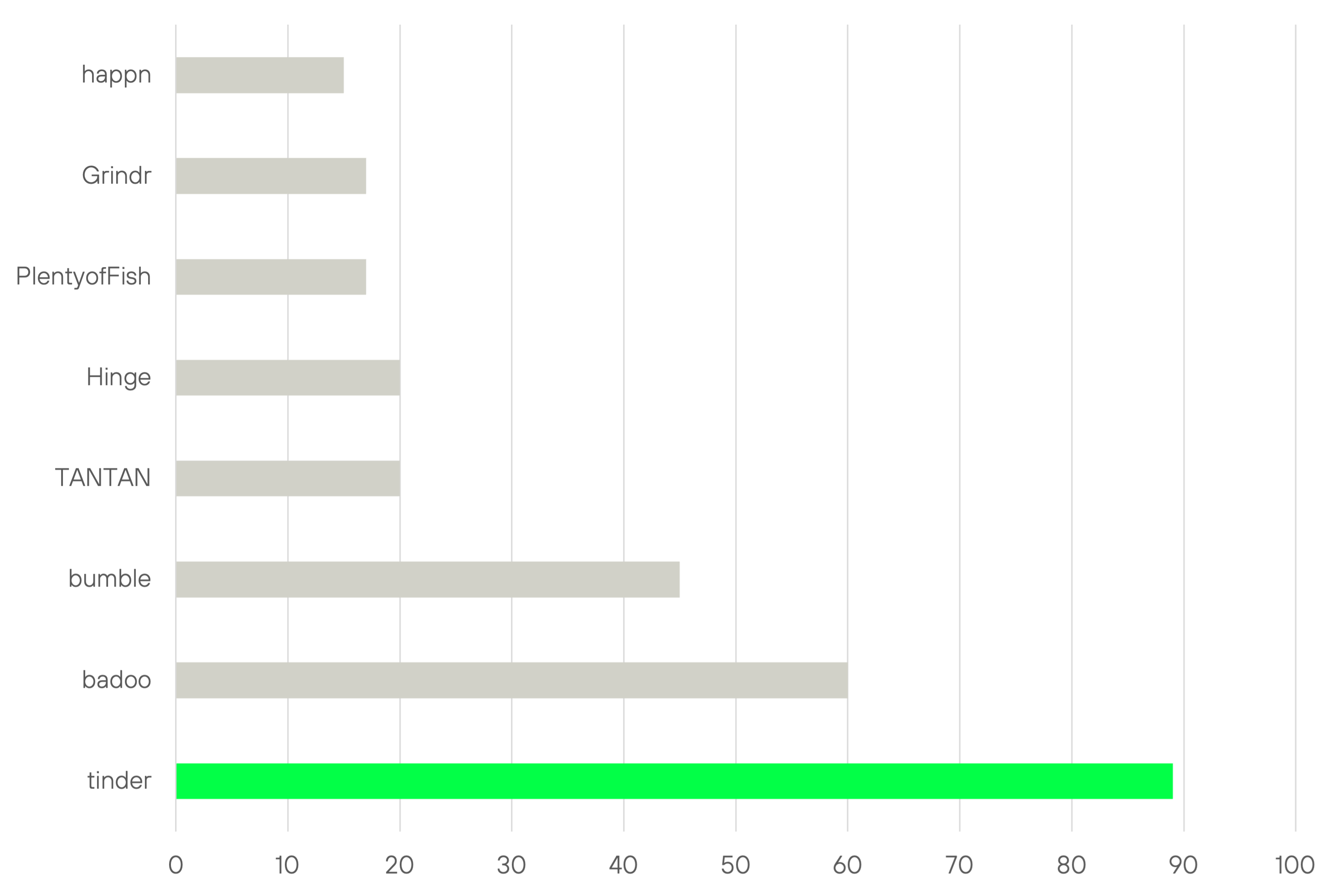
Worldwide, there are over 8.000 dating sites dominated by giants such as Tinder (89M users), Badoo (60M users), Bumble (45M users), Tantan (20M users), Hinge (20M users), Plenty of Fish (17M users), Grindr (the leading LGBTQ site with 15M users) and Happn (15M users). With the exception of Hinge and Plenty of Fish, all dating services have a casual dating focus.
Web2 Online Dating Landscape; users in million
Web2 Online Dating still suffers from major unsolved problems
These are the main problems and challenges of the industry:
- Catfishing, lies, and fake profiles
- Online and offline harassment
- Romance Scams
- Imbalance of female and male users
1. Catfishing, lies, and fake profiles
Catfishing is a process of luring someone into a relationship by means of a fictional online persona or a fake identity. Today, it is estimated that 10% of profiles are fake. In addition, 57% of dating users confess to lying on their profiles which might lead to the fact that the number of fake profiles is even higher. This refers to information regarding height, marital status, name, interests, education, and job profiles. Not only are they against most dating services’ terms of use, but fake profiles also have a detrimental effect on the overall quality of the dating service. The more experience with fake profiles users have, the lower the success rate and the lower the trust and retention of the dating service. In some cases, Web2 dating portals are using fake profiles to monetize their existing user base. For example, German dating site Amourny is alleged to have used employees to use fake profiles and chat with users and thereby increasing conversion rates into premium features.
For most dating services, a full KYC procedure is not mandatory for registration. Often email or phone numbers suffice. But even if KYC became mandatory it is unclear how fake profile rates would seriously diminish. However, there is another side to catfishing. People also hide their identities to protect themselves. Anonymity or pseudonymity through the use of profile picture avatars (PFPs) can actually increase safety against doxing (see next paragraph), for instance. Therefore, future dating services need to find the right balance between anonymity and openness.
2.Online and offline harassment
To date, Web2 dating apps have not been doing a good job regarding harassment of female online daters. 57% said they had received unwanted sexually explicit messages or images. 19% between 18-34 were threatened to be physically harmed (vs. 9% male online daters).
In addition to threats and unwanted messages, doxing is increasingly becoming a challenge to primarily female users as well. Doxing involves searching for and publishing private or identifying information about an individual on the internet, typically with malicious intent. According to a survey of security software firm Kaspersky, 16% of users have experienced doxing through dating apps (22% in Asia) leading to 8% of users with intimate photos leaked online.
3.Romance Scams
Romance scams have increased from 2016 to 2020. This is how it works: Bad actors use dating apps to trick their victims into thinking they wish to enter a serious relationship, then demand money from their targets under the pretext that they can’t keep the relationship going without financial help. Users paid a total of $75M to these frauds in 2016, and by 2020, that sum had increased to a staggering $304M. Gift cards and wire transfers are the two most popular ways for scammers to obtain funds, and the average amount in 2020 was a startling $2.5K. The 20 to 29-year-old age group saw the largest increase in reports submitted, with numbers doubling between 2019 and 2020. The most spectacular romance scam is certainly the story of the “Tinder Swindler” Simon Leviev who is estimated to have conned an estimated $10 Million. By pretending to be a diamond millionaire and contacting women on the dating app Tinder he was tricking women into giving him loans that he never paid back.
4.Imbalance between females and males
Most Web2 Online Dating services suffer from a strong imbalance between female and male users. In particular, casual dating apps are highly skewed toward male users. The estimates vary considerably: Tinder has 76% men and 24% women. In contrast, Badoo has 65% men and 35% women. Among the three, Bumble appears to have the evenest distribution, with about 43% women and 57% males. Other sources report Tinder male users to outnumber females even by 9 to 1, with Bumble being the most “female friendly” app with only 20% female users.
Physical attractiveness is the key criterion for male users, women are much more demanding, prioritizing socio-economic attributes when choosing a male partner. Therefore, male users are less picky and swipe right 46% of the time while female users do this only 14% of the time. In addition, men have to send 114 messages to get a response, while women just have to send 25.
Ultimately, on today’s Web2 Online Dating platforms men must spam women to get a response. Naturally, women will react more selectively to the oversupply of messages. “Since women are understandably disinclined to respond to all the messages, men must send out more in order to guarantee any response.” It is a vicious cycle.
Web3 as a solution?
In this section, we discuss how Web3 can help address the challenges described above. We do not claim that Web3 technologies are exclusive solutions to these issues but see it as a complementary approach to the problems of Web2 Online Dating demonstrated above.
We believe that Web3 innovations in the field of Decentralized Identity (DID) and Self Sovereign Identity (SSI) will be the catalyst of the next Web3 Online Dating services. In Web2, data on personal identity is owned by centralized and siloed organizations such as Meta and Alphabet. To remind ourselves, it was Facebook that sold private user data to Cambridge Analytica in 2010 which exploited personal data of 87M people for political advertising purposes. The next generation of Online Dating services will use Web3 features in the area of decentral identities to address challenges discussed above and privacy issues that deal with issuance, acceptance, control, expiration, discoverability, searchability and trust of personal data.
Before we dive into the concrete application, we give an overview of the main streams of Web3 data and privacy solutions.
Decentralized Identity (DID) and Verifiable Credentials (VCs)
Web3 postulates that personal identity and associated data should be owned and controlled by the actual persons themselves via DIDs and VCs. This should be done in a decentralized manner without the need for a central registry. DIDs are unique identifiers that enable an entity to be identified in a manner that is verifiable and persistent (as long as the DID controller desires). They are like an alias for an Ethereum or Bitcoin address, PGP key, or other cryptographic identifiers that prove ownership and control over other identifiers and data. VCs are encrypted, tamper-proof messages written by one DID about another or itself. It is a W3C open standard for digital credentials that act as a badge or license.
Anyone can issue verifiable credentials about anything, and these credentials can be presented to and verified by anyone. The party that creates the credential is referred to as the issuer. The credential is subsequently provided to the holder, who stores it for future use. By presenting their credentials to a verifier, the holder can demonstrate something about themselves. Examples for VC claims include:
- Education: University degrees, certificates, courses
- Ownership: Bank account, citizenship, residence, property, car, assets
- Personal: Age, height, weight, blood type, job records, employment
- Events: Attendance of online and/or offline events or conferences
DIDs, VCs and Zero Knowledge Proofs
DIDs, VCs in conjunction with Zero Knowledge Proofs (ZK Proofs) can be very effective and efficient. ZK Proofs provide a means of validating data and communicating it with a third party without actually disclosing the data. In other words, it allows users to share sensitive information without sharing the data itself. Instead, a cryptographic proof is conveyed that proves the claim that is made and without leaking the data itself. Zero Knowledge Proofs effectively provide a riskless way to share data. To give an example, Alice could prove that she is Alice with her social security number by using a zk-SNARK (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge). In this case, the verifier can never access the social security number.
Soulbound Tokens (SBTs)
SBTs, a concept invented by Vitalik Buterin, are non-transferable and public-verifiable non-fungible tokens that can be used for immutable records such as employment history, work experience, and academic credentials. Similar to VCs they act as Proof of Knowledge for credentials like education, professional records (as a digital resume), and mementos of attendance to major programs. As of now, there is no ERC standard for SBTs with most SBTs being built on ERC-721 with mintability and voting. Web3 builders like CAN focus on EIP-4671 (non-tradable tokens standard), EIP-4973 (account-bound tokens), EIP-5192 (minimal soulbound NFTs).
SBTs differ from DID & VCs such that SBTs are immutable, fully on-chain, and thus publicly visible with their verification taking place off-chain. Therefore, the fact that SBTs represent Personal Identifiable Information (PII) and ultimately all transactions are stored indefinitely on-chain has sparked quite a bit of controversy. Also, loss of keys could in theory lead to a loss of “soul” for which Buterin suggests implementing “guardians” that make sure keys could be recovered.
The advantages of VCs are that they offer interoperability, which means that they are not permanently tied to a specific blockchain. VCs also provide users with greater privacy since they can choose which information to store locally on their device or backup server, rather than permanently on the blockchain. In addition, VCs offer higher scalability since off-chain transactions reduce gas fees and overall costs.
On the other hand, SBTs have advantages of their own. Because SBTs are already on-chain, they can be easily integrated with existing protocols, making them highly composable. Furthermore, issuing entities can use regular smart contracts to verify certain criteria, which eliminates the need for a separate decentralized network to verify issuers, resulting in a more decentralized system.
POAP – Proof of Attendance
Launched in August 2021, POAP is a protocol that produces digital badges or collectibles. These collectibles, also known as POAPs, are created as non-fungible tokens (NFTs) through the use of smart contracts on the Ethereum blockchain. They are ERC-721 tokens designed to commemorate and document event attendance. Their goal is to provide evidence that the holder was present at a specific event or conference. Since it is an NFT, the POAP can be easily transferred even though it has a unique serial number and is immutable itself. In the future, we expect POAPs to be combined with SBTs so that they become a more reliable proof of personal attendance.
Application of Web3 and Feature Ideas
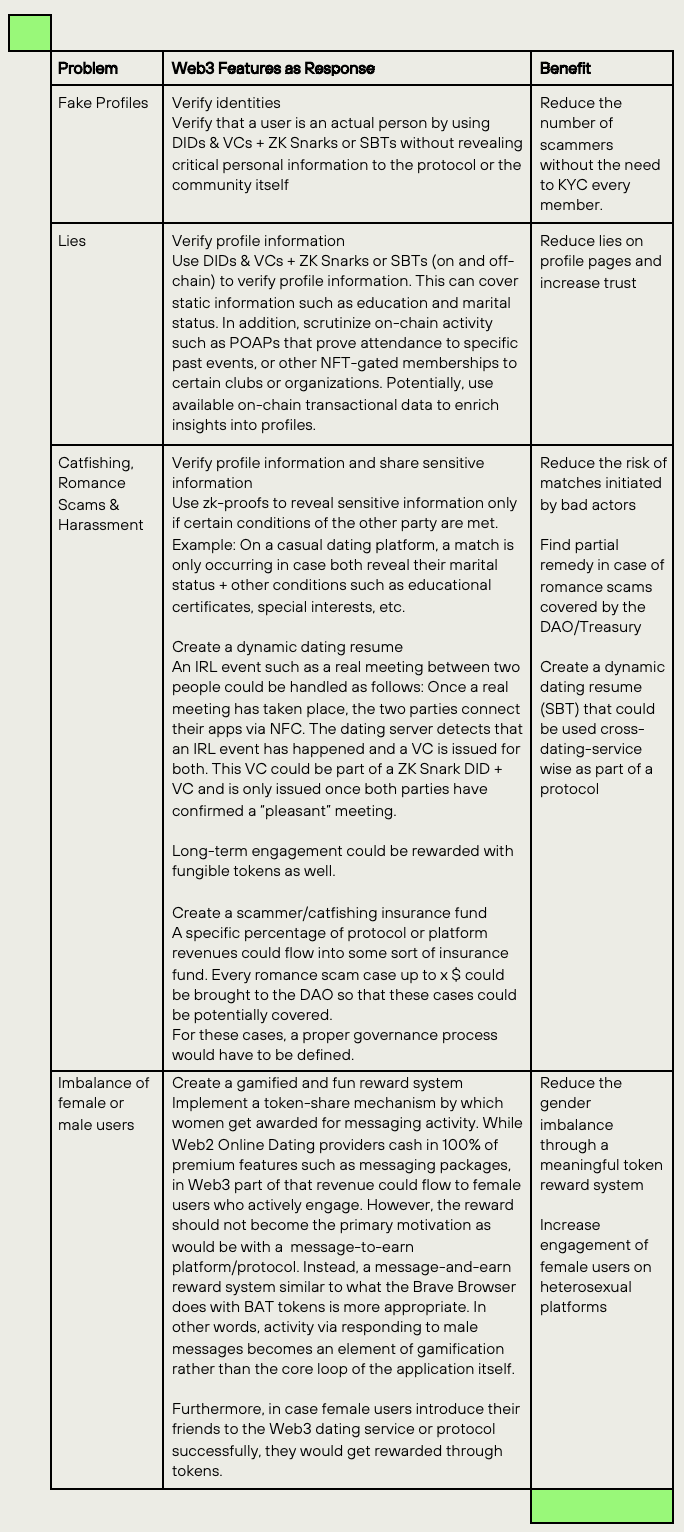
This section discusses how Web3 technologies and features can improve in the area of digital identity, verification of profiles, the creation of a dynamic dating resume, protection mechanisms such as a catfishing/scam insurance fund and a token-based reward system that could improve the gender imbalance on most Web2 Online Dating Services.
Conclusion
This article is a discussion about the current challenges of Web2 Online Dating and how Web3 features can alleviate those problems. Most of the issues are fundamentally grounded in an identity system that promotes fake profiles, scamming, catfishing, bad actors in online and offline harassment, and romance scams. We believe that in addition to business model innovation, advanced analytics and machine learning Web3 technologies based on DID, Verifiable Credentials, SBTs, and POAPs could become the fundament of such a solution package but need adoption to the very specific use cases of Online Dating.
First, trust and authenticity can be increased through DIDs, VCs, and SBTs. In particular, we view the application of ZK Snarks which potentially verify identities, and valuable profile information by only sharing cryptographic proofs as a huge opportunity in the dating segment. Matching rates could thereby be improved by the fact that Alice’s special “kinks” are only revealed if Bob’s kinks are revealed too in combination with other VCs that must be met in order for the match to happen.
Second, we view great potential in the creation of a dynamic dating online resume itself, in which users control specific data, yet are rewarded for actual and genuine activity such as IRL meetings which generate a POAP for instance.
Third, we also suggest implementing Web3 mechanisms such as insurance funds that could deal with real romance and catfishing scams that are governed by and financially covered by the DAO.
Fourth, we advocate a token-based reward system that is based on a message-and-earn mechanism which would improve the gender imbalance toward a better ratio without making it the primary motivation driver behind platform activity.
Fifth, we do not claim Web3 to be the exclusive solution to the challenges described above. We expect both Web2 startups and academia to continue innovating the space. For example, start-ups such as Hulah aim to reduce catfishing by only allowing male users to join the platform in case they were invited by female users that are already on the platform. The Christian dating platform Salt attempts only to connect people of the same religion. Dating has always attracted the interest of academics, too. Researchers at the University of Dallas have found a way to dynamically account for preferences, behavior, and activity metrics of users to improve the operational efficiency of matching platforms. In field experiments, they were able to improve matching algorithms by 27% compared to the existing algorithm operated by Cupid. These are examples of business model innovation and the use of advanced analytics that may improve user experiences of online dating services in the future.
Lastly, we welcome any founders who would like to engage with the issues addressed in this article and provide solutions as to how they would implement a Web3 dating protocol or platform. We have deliberately not discussed how DIDs, VCs, or SBTs, and POAPs could be implemented in detail. Rather, this article is a call to action and food for thought for future entrepreneurs who want to disrupt Web2 Online Dating.
We are happy to discuss your ideas and pitch decks with us!
Special Thanks to Christoph Rosenmayr for the contribution to this article.